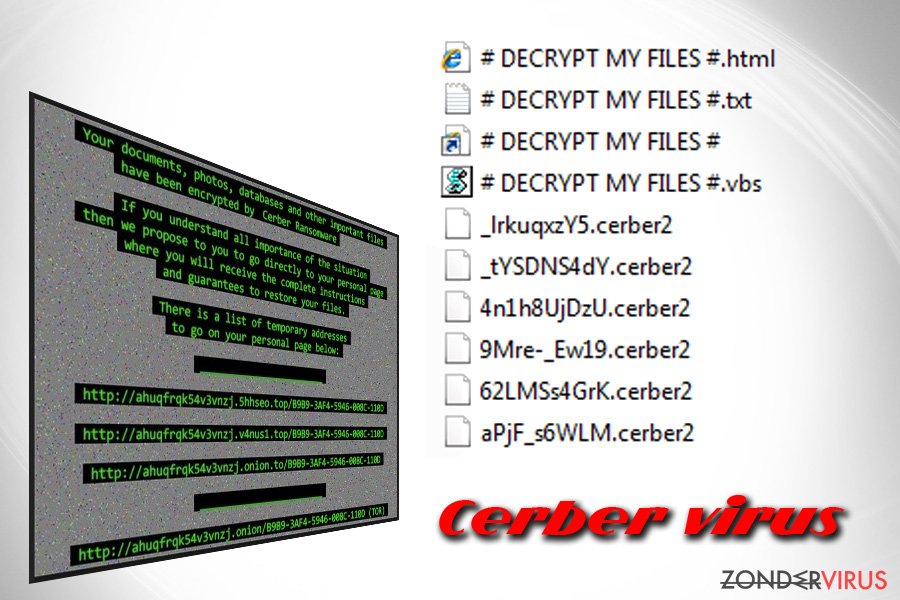
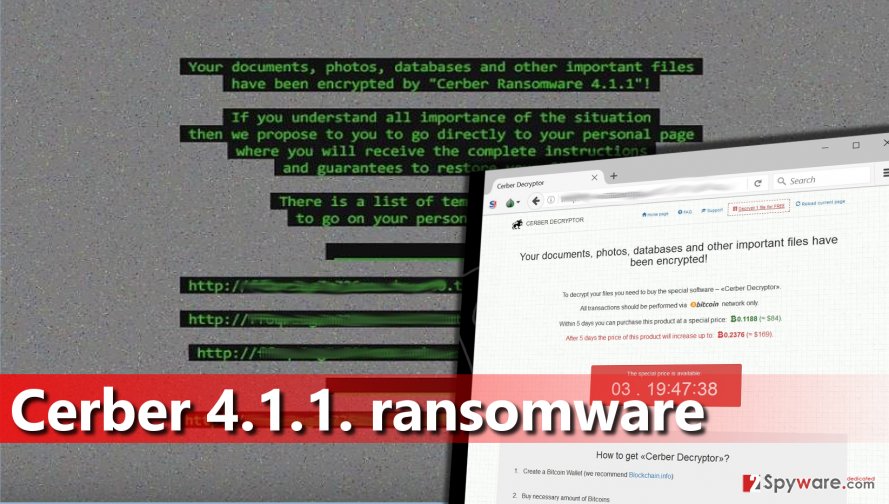
Cerber ransomware - Cerber Ransomware [Updated]
Cerber Dropper Ransomware Analysis
The best strategic cybersecurity capability process includes elements to Predict, Prevent, Detect, and Respond to risks.
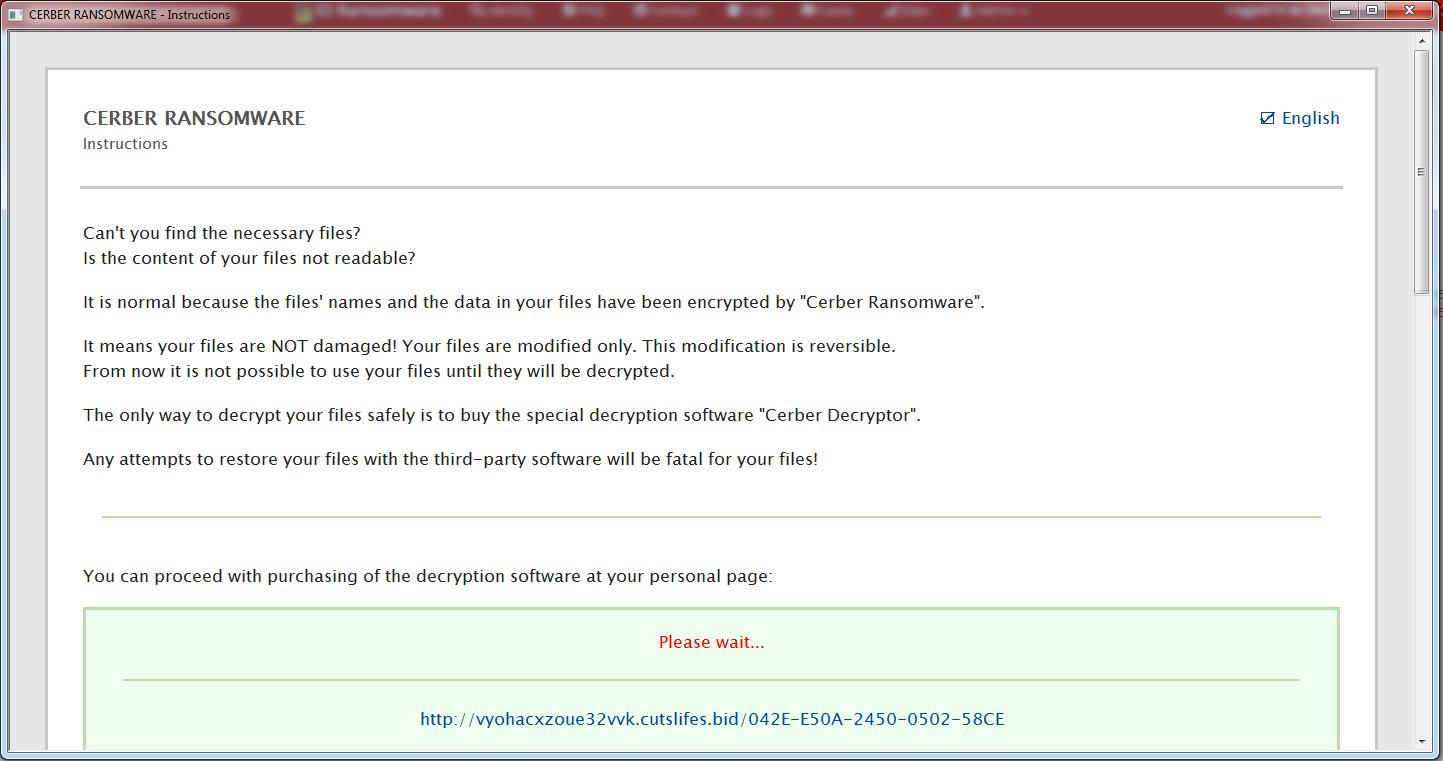
However, there is currently no automatic decryption tool for.
Users and businesses can also benefit from a multilayered approach to security that covers the , , , and.
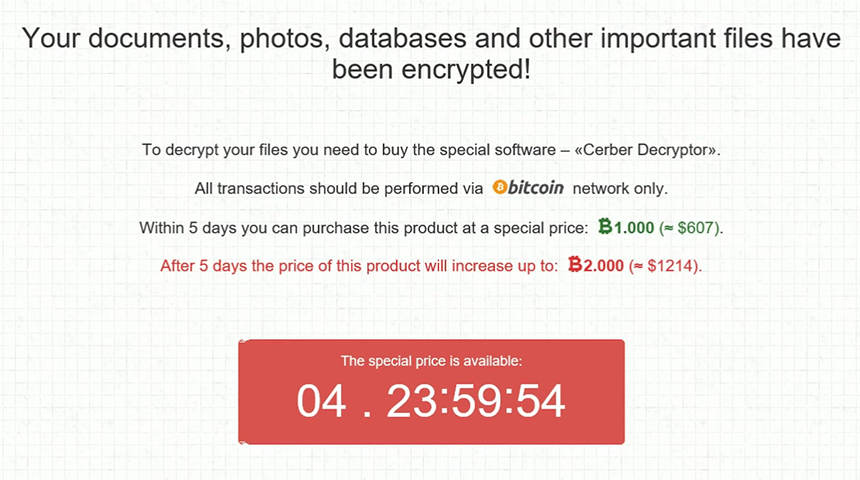
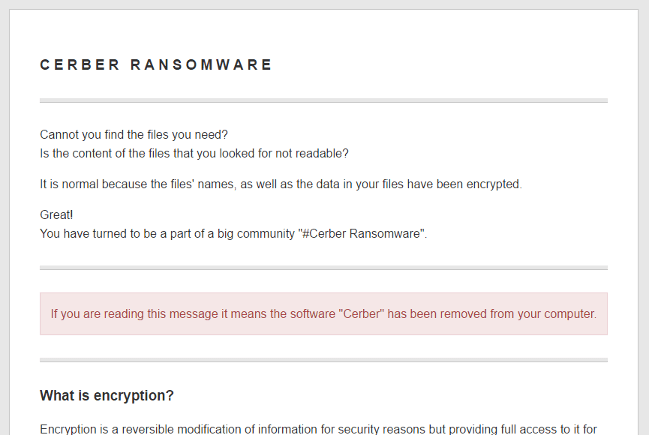
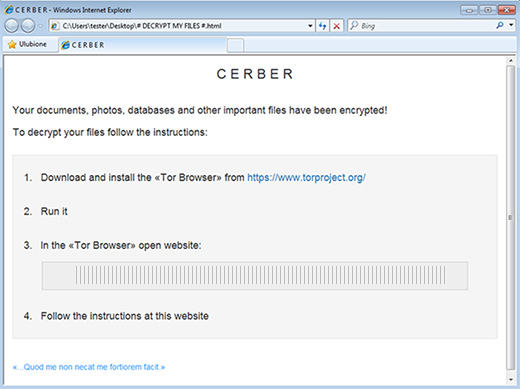
How to remove Cerber ransomware and decrypt .cerber files
Just make sure you obliterate the crypto virus before downloading unaffected copies of your files.
Figure 27: Executing encryption routine in threaded mode based on number of processors File encryption process File encryption is carried out in stages.
If these unfavorable requirements are met, the machine becomes infected without any obvious indicators of compromise.
- Related articles
2022 blog.mizukinana.jp